Imagine you’re accessing your favorite crypto site and suddenly your digital wallet balance disappears without a trace. You start to wonder, “What happened?”
It turns out, it could be the result of a DNS hijacking attack, a type of cyberattack that is increasingly prevalent and dangerous, especially for active crypto users.
In a world that is increasingly dependent on blockchain and Web3 technology, attacks on the domain name management system (DNS) can be fatal.
This article will discuss how DNS hijacking attacks work, their impact on digital assets, and strategies to protect yourself from this threat.
What is DNS Hijacking?
DNS (Domain Name System) is a system that functions to change the domain name that we type, such as www.google.com, into an IP address used by the server to connect us to the website.
If there was no DNS, every time we wanted to open a site, we would have to memorize and type in a series of IP numbers.
The presence of DNS makes the experience of surfing the internet more practical because we only need to use a site name that is easy to remember.
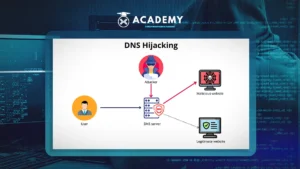
Meanwhile, DNS Hijacking is a type of attack where an attacker changes DNS settings to direct users to unwanted or dangerous sites.
In this attack, the user’s internet traffic can be redirected to a fake site that looks like the original site, without the user’s knowledge or consent.
The goal can be to steal data, login credentials, or even divert the user’s crypto funds to the attacker’s account.
DNS Hijacking, DNS Spoofing, and Phishing attacks may look similar, but they work differently.
DNS Hijacking occurs when DNS settings are changed to redirect users to fake sites that look authentic. This allows attackers to steal personal data or credentials without the user realizing it.
Meanwhile, DNS Spoofing (or DNS cache poisoning) injects fake data into the DNS cache, which causes legitimate requests to be redirected to the wrong or fake site.
Phishing is different because attackers create fake websites that look like the real ones and trick users into entering their personal data. This attack is often carried out through fake emails or messages that lead to fake sites.
Basically, all three are equally dangerous, but each uses different techniques to steal sensitive information.
Other Interesting Articles For You: What Is Crypto Phishing and How Does Phishing Work?
How DNS Hijacking Works
DNS Hijacking is a sophisticated and dangerous attack in which an attacker changes DNS settings to redirect users to a site they control.
While users intend to access a legitimate site, they are instead redirected to a fake site that has been prepared by the attacker.
This attack can steal sensitive information, such as login credentials or personal data, without the user even realizing it.
The process begins with a change in the DNS resolver, which is usually done by infiltrating the DNS settings on the user’s server or router.
Once the DNS settings have been successfully changed, all of the user’s internet requests are redirected to a server controlled by the attacker instead of the real server that is supposed to serve the request.
At this point, users who try to access a website, such as a crypto exchange, will be redirected to a fake site that looks very similar to the real site.
This fake site is designed to steal sensitive information, such as login credentials or private keys.
In fact, even though it looks like the user is accessing a secure site, they have actually fallen into the attacker’s trap.
Attackers can also use DNS reply forgery to replace the correct IP address with one that points to a site they control.
In addition, they can manipulate the DNS cache on the server or user’s device, which means that even after the attack is complete, users are still redirected to fake sites because the fake information is stored in the cache.
It is important to note that there are several types of attacks that are often used in DNS Hijacking. One of them is router hijacking, where the attacker changes the DNS settings on the user’s router.
It forces all devices connected to the network to use a DNS server that has been controlled by the attacker. In this way, they can redirect all user internet traffic to a fake site that they control.
In addition, there is also a Man-in-the-Middle attack, where the attacker intercepts communication between the user and the DNS server, then modifies the DNS request or reply to redirect traffic.
Another technique is DNS cache poisoning, where the attacker injects fake information into the DNS cache, to ensure that users are still redirected to fake sites even though they are trying to access legitimate sites.
One real-life example of a DNS Hijacking attack occurred on crypto wallet users. Attackers hack into a user’s router or DNS server and redirect them to a fake site that looks like a legitimate crypto exchange.
Unbeknownst to them, the user then enters their credentials on the fake site, which is then used by the attacker to access and steal the crypto funds in the user’s wallet.
This is an example of how dangerous DNS Hijacking attacks are and the reason behind the importance of keeping your DNS settings secure.
Also read related articles: 14 Security Terms in the Crypto World & Complete Tips to Prevent Them
The Dangers of DNS Hijacking for the Crypto World
DNS hijacking is a major threat in the crypto world, with the potential for very detrimental risks to users and related platforms.
In this attack, attackers can manipulate DNS to redirect users to fake, malicious sites, causing major financial losses.
It not only threatens individuals using crypto wallets, but also affects exchanges and DeFi protocols that rely on secure DNS infrastructure.
Several real-life cases, such as the attacks on Cream Finance and PancakeSwap in 2021, and Polygon and Fantom in 2022, show how attackers can redirect users to fake sites.
These attacks are known to allow attackers to steal users’ seed phrases and drain their wallets.
The types of DNS hijacking attacks themselves are divided into several types, one of which is local DNS hijack, where malware is installed on the user’s device to change local DNS settings.
Then there is router DNS hijack, where attackers change DNS settings on the router to affect all connected devices.
Next, there are man-in-the-middle DNS attacks, where attackers intercept communications between users and DNS servers.
Finally, there are rogue DNS servers, where DNS servers are compromised to change settings and redirect traffic to malicious sites.
These attacks are often used for phishing and malware distribution, which is very detrimental to the crypto world.
For example, in 2021, Cream Finance and PancakeSwap were attacked by DNS hijacking that redirected users to fake sites to steal their seed phrases and digital assets.
Similarly, Polygon and Fantom also fell victim to similar attacks, where users were redirected to malicious sites and lost their funds.
These incidents underscore the importance of better DNS security, both on the part of users and service providers, to avoid greater losses.
How to Detect DNS Hijacking

DNS Hijacking can cause a number of changes that are not obvious to the average user, but there are some signs to look out for.
One of them is an unusual site redirect, where the user is directed to a different page than expected even though the URL entered is the same.
In addition, an invalid SSL certificate or security warnings when accessing the site can also be an indicator of a problem with the DNS system.
Another sign is a change in the appearance of the user interface (UI) that does not match the official design or logo of the site.
To further detect a DNS hijacking attack, there are several tools that can be used.
Whois allows you to check information related to the domain owner and ensure that the DNS settings have not been changed by unauthorized parties.
On the other hand, dig and nslookup are tools that can help check whether the DNS server used is really appropriate and points to a legitimate address.
In addition, performing a DNS leak test can help detect DNS leaks that may occur due to this attack.
By utilizing these tools, detection and prevention of potential DNS hijacking threats can be done more effectively.
Another interesting article for you: Giveaway Scam: Fraudulent Mode Under the Guise of Free Gifts & How to Avoid It
How to Prevent DNS Hijacking (Proactive Steps)
To prevent DNS hijacking, there are several proactive steps that can be taken, including the following:
1. Use Encrypted DNS (DoH and DoT)
DNS over HTTPS (DoH) and DNS over TLS (DoT) are protocols that encrypt DNS traffic, preventing hackers from monitoring or changing DNS queries.
2. Always Enable 2FA for Important Accounts
Enabling two-factor authentication (2FA) on important accounts can provide an additional layer of protection so that even if account credentials are leaked, hackers still cannot access them.
3. Update Router Firmware and DNS Regularly
Updating router firmware and DNS settings regularly can patch security holes and prevent exploitation by irresponsible parties.
4. Use a VPN with DNS Leak Protection
A VPN equipped with DNS leak protection will ensure that all DNS requests are made through a secure and encrypted server, avoiding potential hacking.
5. Don’t Click Random Links, Especially from Suspicious Emails
Avoid clicking on links from suspicious emails or messages because this can lead to phishing or DNS redirection to malicious sites controlled by the attacker.
What to Do if You Become a Victim?
If you are suspected of being a victim of DNS hijacking, here are the steps that must be taken immediately, namely:
1. Disconnect Connection Immediately
Immediately turn off the internet connection to prevent attackers from further accessing sensitive data or information.
2. Reset DNS and Router
Change the DNS settings on the device and router to return the settings to a safe state, and make sure the router is not using an infected DNS.
3. Report the Incident to the Service Provider
Contact your internet service provider (ISP) or DNS provider to report the incident and ask for help in resolving this issue.
4. Check Wallet Activity if Related to Crypto
If related to digital assets, you should immediately check wallet activity to detect unauthorized transactions or suspicious fund movements.
5. Data Backup and Complete Security Audit
Back up important data and perform a complete security audit on the device to ensure no malware or security holes are left behind.
Conclusion
Well, that was an interesting discussion about DNS Hijacking: A Cunning Attack That Makes Crypto Collapse! & How to Prevent It which you can read in full at the Crypto Academy at INDODAX Academy. Not only does it increase your insight into investment, here you can also find the latest crypto news about the crypto world.
And for an easy and safe trading experience, download the best crypto application from INDODAX on the App Store or Google Play Store. You can also start buying Bitcoin, buying Ethereum, and other crypto assets practically in your grasp at INDODAX Market. Also follow INDODAX’s social media here: Instagram, X, Youtube & Telegram
In conclusion, DNS Hijacking is not only a technical threat, but also a structured attack that can threaten financial security, especially in the crypto world.
By recognizing the characteristics of this attack early on and implementing the right protection, you can protect your digital assets amidst the ever-growing cyber risks.
Education will be the first line of defense and this article is the first step to becoming a smarter and safer crypto user.
FAQ
1.What is DNS Hijacking?
DNS Hijacking is a cyberattack that manipulates DNS so that users are directed to fake sites without realizing it.
2.How is it different from regular Phishing?
DNS Hijacking works at the domain system level, making users open fake sites even though they type the original URL, while phishing often goes through suspicious links.
3.What is the impact on crypto users?
You can lose digital assets because you enter a fake wallet or exchange site that looks real.
4.How to detect DNS Hijacking?
Pay attention to changes in the appearance of the site, suspicious URL addresses, or invalid SSL. Use tools like nslookup to check the DNS IP.
5.What is the best way to prevent it?
Use encrypted DNS (DoH), enable 2FA, update your router, and avoid connections from public or unsecured networks.
Author: BOY





 Polkadot 8.91%
Polkadot 8.91%
 BNB 0.54%
BNB 0.54%
 Solana 4.81%
Solana 4.81%
 Ethereum 2.37%
Ethereum 2.37%
 Cardano 1.35%
Cardano 1.35%
 Polygon Ecosystem Token 2.11%
Polygon Ecosystem Token 2.11%
 Tron 2.85%
Tron 2.85%
 Market
Market


